How Do You Know Packet Is Icmp From Hex
Network Bundle Manual Analysis
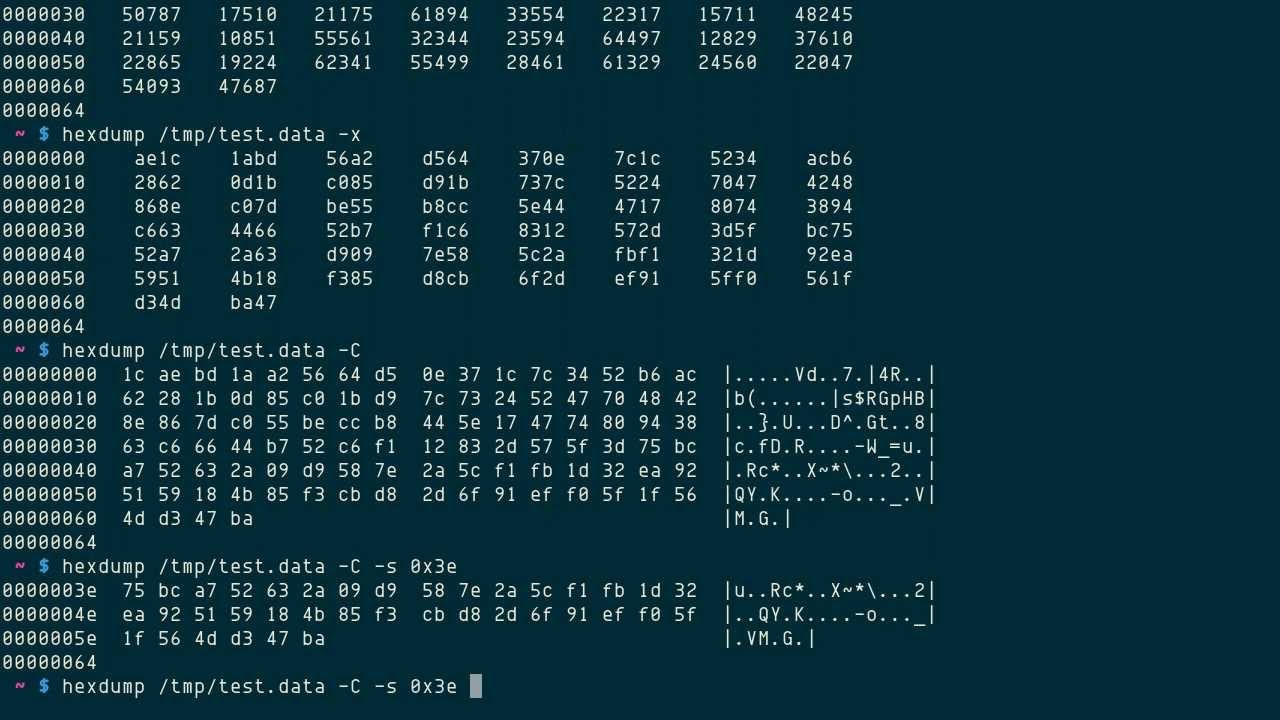
One of the essential skills that an analyst or a forensics investigator has to be equipped with is interpreting hexadecimal raw files. Doing a transmission analysis of network packets without any tools would be a good commencement to get yourself comfortable with the hexadecimal representation of the files, and of course, it will make y'all empathise the network traffic better and go a sense of what a normal traffic would wait like inside your network.
NOTE: I wait you to exist familiar with converting hexadecimal to decimal and vice versa, if not I propose you to have a wait at this tutorial https://www.tutorialspoint.com/how-to-convert-hexadecimal-to-decimal
The Frame Anatomy
A frame is a container of a unmarried network packet that is ready to be transmitted into the network medium or just been received.
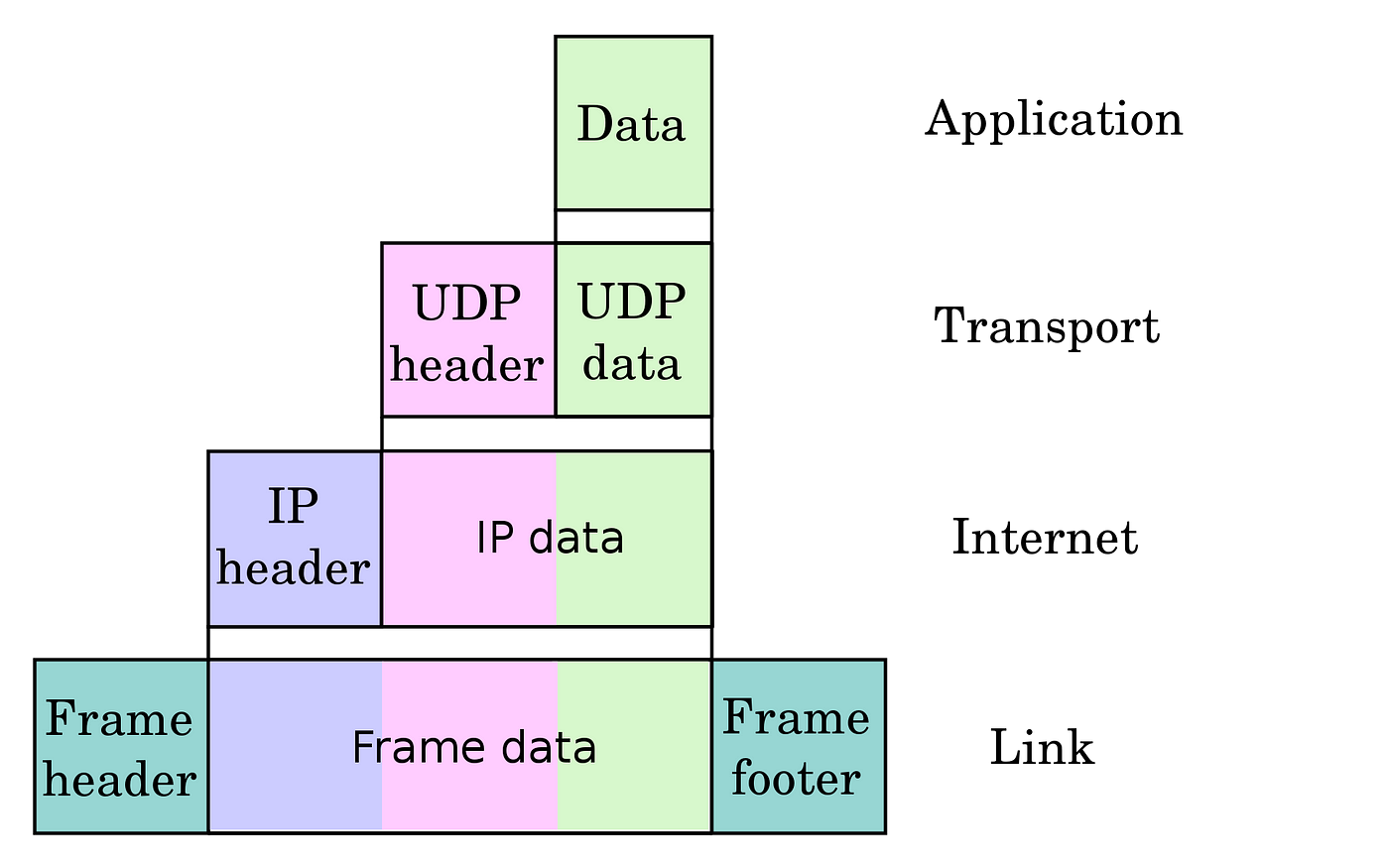
Inside the frame which is a layer-2 data unit, we expect to find a frame header that encapsulates a packet, which is a layer-iii data unit (normally, IP) that contains a layer 3 header encapsulating a segment, which is a layer-4 data unit (TCP/UDP) that consists of a header that may encapsulate a payload (data). I assume that you accept the necessary networking background so I'll non explain the OSI layers.
Some Useful Tips
- i byte = viii bits
- i byte = 1 octet
- four bits = 1 nibble = 1 hex graphic symbol.
- You can e'er use this site hpd.gasmi.net to make sure of your interpretation.
- Always refer to the RFCs, it may be overwhelming at outset but believe me, it is the best resource out there.
- I suggest you read and practise the labs of the Applied Packet Analysis volume by Chris Sanders. Information technology'll get you very comfortable using Wireshark to analyze network traffic. Annotation: The hexadecimal analysis is out of the scope of this volume.
Ethernet Frame
The very first bunch of hex characters (usually, 14 bytes) that you'll run across in whatever raw packet belong to the ethernet header. In the IEEE 802.three standard documentation, you lot will find many fields merely in your real alive captures, you may non be able to run into all of them considering some of the fields such as Preamble and SFD are beingness used for establishing synchronization in layer ane so, they never go to the memory. Commonly, yous'll meet it like this:
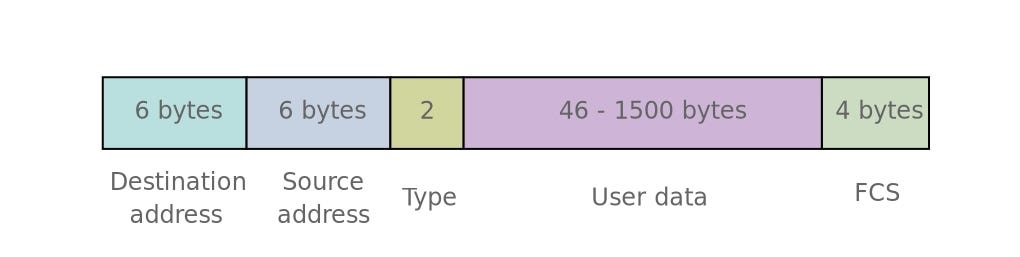
- Destination MAC Address: 6-bytes that represents the 48-bit destination MAC accost. Notation: an
ff ff ff ff ff ffdestination MAC means that this is a broadcast message which will be sent to all the devices in the broadcast domain . - Source MAC Address: six-bytes that represents the 48-scrap source MAC address.
- Type: A 2-bytes number that represents the protocol that has been used to send that specific frame. By and large, information technology'll exist
08 00for IPv4 and86 ddfor IPv6 you can find a listing of the protocol types hither https://www.iana.org/assignments/ieee-802-numbers/ieee-802-numbers.xhtml - Information: A variable-length field between 46 to 1500 bytes that contain the encapsulated data from the higher layers.
- Frame Cheque Sequence (FCS): 4-bytes that are existence used for detecting errors in the frame. Those 4 bytes correspond the frame trailer (located afterward the data).
For example, allow's attempt to analyze this elementary bundle and figure out what information it contains:
0x0000 00 21 29 66 71 95 00 25 b3 bf 91 ee 08 00 45 00
0x0010 00 3c 72 8d 00 00 80 01 00 00 0a 0a 00 03 c0 a8
0x0020 00 80 08 00 4d 36 00 01 00 25 61 62 63 64 65 66
0x0030 67 68 69 6a 6b 6c 6d 6e 6f 70 71 72 73 74 75 76
0x0040 77 61 62 63 64 65 66 67 68 69 The first six bytes are the destination MAC address 00 21 29 66 71 95 followed by another half dozen bytes representing the sender MAC address 00 25 b3 bf 91 ee . the outset 3 bytes of the MAC address represents the OUI (Organizationally Unique Identifier) which is a unique identifier for each manufacturer followed by another three bytes that stand for the HUI (Host unique identifier) which is a unique identifier for each NIC per manufacturer. so,
- The Destination Mac:
00:21:29:66:71:95 - The Destination OUI:
00:21:29 - The Destination HUI:
66:71:95 - The Source Mac:
00:25:b3:bf:91:ee - The Source OUI:
00:25:b3 - The Source HUI:
bf:91:ee
The following two bytes are 08 00 which indicates that IPv4 was used for sending the packet.
Hence, we can conclude that the following bytes are the data (the Layer 3 packet).
IPv4 Package
There are ii types of IP protocol IPv4 and IPv6. For simplicity, permit's analyze the IPv4 at present and nosotros may analyze the IPv6 in another story.
Co-ordinate to the RFC 791 — Internet Protocol, section 3.one: Internet Header Format a summary of the contents of the internet header follows:
0 one 2 iii
0 1 2 3 iv five 6 7 8 9 0 one 2 3 4 v half dozen 7 viii nine 0 1 2 3 4 5 6 seven 8 nine 0 1
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
|Version| IHL |Type of Service| Total Length |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Identification |Flags| Fragment Offset |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Time to Live | Protocol | Header Checksum |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Source Accost |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Destination Address |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Options | Padding |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ Note: each tick marking represents a one-scrap position.
- Version: (4 bits, 1 hex character) indicates which blazon of the IP protocol was used.
4indicates IPv4 and6indicates IPv6 - IHL (Internet Header Length): (iv bits, 1 hex grapheme) indicates the header length in 32-flake words, in other words, how many 4-bytes are occupied by the header? Notation: The minimum value for this field is 5, which indicates a length of v × 32 bits = 160 $.25 = 20 bytes. As a 4-fleck field, the maximum value is 15, this means that the maximum size of the IPv4 header is 15 × 32 bits, or 480 $.25 = threescore bytes.
- Type of Service: (8 bits, 2 hex characters) has had various purposes over the years and has been divers in different ways past five RFCs and it's very rarely used today and so we'll not hash out it here. You lot tin can refer to Section 22 in RFC 3168 for the historical definition for the IPv4 TOS octet.
- Total Length: (16 bits, 4 hex characters) represents the total length of the packet (Header + Data). Of course, it is represented in hexadecimal and then, you'll need to convert it to decimal to know the verbal length. Note: the minimum value is
00 14which indicates a length of 20 bytes (a header without data), the maximum value isffffwhich indicates a maximum length of 65,535 bytes - Identification (IPID): (16 bits, 4 hex characters) A unique identification number used to place a packet or sequence of fragmented packets.
- Flags: (3 $.25) Used to identify whether a package is part of a sequence of fragmented packets. Flake 0: reserved, must be zero
Bit ane: (DF) 0 = May Fragment, 1 = Don't Fragment.
Bit 2: (MF) 0 = Concluding Fragment, i = More Fragments.
0 1 2
+---+---+---+
| | D | M |
| 0 | F | F |
+---+---+---+ For fragmented packets, all fragments except the last have the MF flag set. The final fragment has a flags-value of zero and a non-zero Fragment Starting time field, differentiating it from an unfragmented packet. If the bundle is marked as DF and has no outset, it will take the value of 40 00 NOTE: fragmentation is being maliciously used for diverse intentions similar IDS/IPS evasion and mounting DoS attacks.
The bit 0 was introduced as an Apr Fools' joke, proposed for use in RFC 3514 every bit the "Evil flake". be used to point whether a packet had been sent with malicious intent, thus making computer security engineering an piece of cake trouble — only ignore any messages with the evil bit set and trust the rest.
- Fragment Offset: (thirteen bits) If a packet is fragmented, the value of this field is used to reassemble the packets in the correct society. NOTE: the flags + the fragment offsets = xvi bits which ways 4 hex characters. to analyze these fields, you need first to convert the sixteen-bits value to binary.
- Time To Live (TTL): (8 bits, 2 hex characters) Defines the lifetime of the parcel, measured in hops. If this field contains the value zero, and so the datagram must be destroyed.
- Protocol: (8 bits, 2 hex characters) This field defines the protocol used in the data portion of the IP datagram. Commonly, it'll be
06indicating TCP,17indicating UDP, and01indicating ICMP, notwithstanding, You can refer to RFC 790 — Assigned Numbers for the protocol numbers. - Header Checksum: (16 bits, 4 hex characters) A checksum on the header only. Since some header fields change (e.g., time to alive), this is recomputed and verified at each signal that the cyberspace header is processed.
- Source Address: (32 bits, 8 hex characters) the source IP Address.
- Destination Address: (32 bits, 8 hex characters) the destination IP Address.
- Options: (variable length) Although options practice have valid uses, specially for network troubleshooting, they are rarely used by legitimate traffic. I'll briefly mention some IP options and I'll permit you imagine how maliciously they can be used, nonetheless, you can refer to RFC 791-Cyberspace Protocol for more information about the IP options.
- Options — Record-Road: tells the router to add its IP address to the options field.
- Options — IP Timestamp: tells the router to write a timestamp into the options field.
- Options — Strict Source Routing: allows the sender to specify the exact route a packet should take to the destination.
- Options — Loose Source Route: allows the sender to specify a listing of routers a packet must laissez passer through. It may also traverse other routers if required.
- Padding: (variable length) It's introduced to ensure that the header contains an integer number of 32-bit words
Finally, the Data! which of grade a layer iv segment.
In our example, we have analyzed the ethernet header of the dump. let'southward extract the IP bundle out of the dump and analyze it.
0x0000 45 00
0x0010 00 3c 72 8d 00 00 80 01 00 00 0a 0a 00 03 c0 a8
0x0020 00 fourscore 08 00 4d 36 00 01 00 25 61 62 63 64 65 66
0x0030 67 68 69 6a 6b 6c 6d 6e 6f 70 71 72 73 74 75 76
0x0040 77 61 62 63 64 65 66 67 68 69 This is a very simple packet, definitely, you will encounter more complicated packets so, you need to determine the IP version (the offset iv $.25) that has been used and the length of the IP header (the second iv bits).
- IP version: iv
- IHL (Net Header Length): 5 × 32 $.25 = 20 bytes
Nosotros but determined that the first 20 bytes of the parcel are the header and the rest of the packet is the data. Why not practice nosotros extract the header for simplicity?!
0x0000 45 00
0x0010 00 3c 72 8d 00 00 80 01 00 00 0a 0a 00 03 c0 a8
0x0020 00 eighty We'll use the IP header anatomy explained above to clarify this header.
- Blazon of Service:
00Non Set up. - Total Length:
00 3cwhich equals lx in decimal. and indeed the packet is lx-byte long (header + data). - IPID:
72 8d - Flags & Fragment Showtime:
00 00 - Fourth dimension To Live (TTL):
80= 128 (decimal) - Protocol:
01which ICMP. wait, what?! a layer-three protocol is encapsulated inside an IP packet! nosotros'll discuss it. 😉 - CheckSum:
00 00Validation Disabled. - Source IP:
0a 0a 00 03y'all need to convert each octet on its own to convert information technology into the decimal representation of the IP and so the IP will be x.10.0.iii - Destination IP:
c0 a8 00 lxxxwhich is 192.168.0.128
Evidently, this packet doesn't take whatsoever options nor padding. Form our analysis, nosotros concluded that this specific packet contains an ICMP protocol data and then, why not we understand the anatomy of the ICMP header?!
ICMP
Although the ICMP is a layer-iii protocol, it is being encapsulated within an IP Packet which is quite odd as the IP packet encapsulates a layer-4 segment!
By the definition of RFC 792-Internet Command Message Protocol, ICMP, uses the basic back up of IP as if it were a higher-level protocol, withal, ICMP is actually an integral part of IP. The Internet Protocol is not designed to be absolutely reliable. The purpose of these command messages is to provide feedback about issues in the communication environment, not to make IP reliable.
There are many types of ICMP letters just we are going to talk over the one that we need in our analysis example. however, I encourage yous to take a await at the residual of them on the RFC 792-Internet Control Message Protocol.
The header of the ICMP will vary according to the message type. but the commencement 4 bytes volition always be the same.
0 1 2 iii
0 1 2 3 4 5 6 7 8 9 0 1 2 three four five 6 seven 8 9 0 1 2 three iv 5 6 7 8 9 0 1
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Type | Code | Checksum |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ - Blazon: the ICMP type
- Code: the ICMP subtype code
- Checksum: this is being used for error detection. Information technology is calculated from the ICMP header and data with value 0 substituted for this field.
Yous can refer to the Net Control Message Protocol page on Wikipedia, Command Messages department for a complete listing of the types and codes.
Repeat and Echo-Reply
The Echo and Echo-Reply letters are being used for the ping command. mainly, to check the connectivity between two hosts.
0 1 two three
0 1 2 iii 4 5 6 seven eight 9 0 1 two 3 four v 6 7 8 9 0 1 two iii four 5 6 7 8 nine 0 i
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Type | Code | Checksum |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Identifier | Sequence Number |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Data ...
+-+-+-+-+- - Type: 8 for an echo message, and 0 for an echo-answer message
- Code: 0 for both echo and echo-reply messages
- The identifier and the Sequence Number: are being to match echos and replies, may equal zero. Annotation: most Linux systems employ a unique identifier for every ping process and an increasing sequence number within that process. Windows uses a stock-still identifier, which varies between Windows versions and a sequence number that is only reset at kicking time. Tin be used for Bone fingerprinting.
- Data: ordinarily, the payload of the packet is generally filled with ASCII characters. The data received in the echo message must be returned in the echo reply message.
In our instance, we have analyzed the ethernet and the IP headers of the dump. let's extract the IP data (the ICMP packet), which is the balance of the packet, out of the dump, and analyze it.
0x0000
0x0010
0x0020 08 00 4d 36 00 01 00 25 61 62 63 64 65 66
0x0030 67 68 69 6a 6b 6c 6d 6e 6f 70 71 72 73 74 75 76
0x0040 77 61 62 63 64 65 66 67 68 69 Unlike the IP header, the ICMP header does not reserve a field for the header length because it varies depends on the message type. One time we determine the message blazon, nosotros tin anticipate the showtime of the data. so, let's begin with determining the message type:
- Type:
08which is an echo request message. hence, the data should be at ninth-byte. In your investigations, you need to analyze the information to detect attacks and security incidents such as tunneling. Sound like some other interesting story. 🤔 - Code:
00 - Checksum:
4d 36 - Identifier:
00 01 - Sequence Number:
00 25
Here we are, we managed to parse a bunch of hexadecimal numbers indicating interesting information. Merely similar the computer does! Very easy and straight frontward, isn't it?
Can you Analyze the following packet on your own? do yourself a favor and try 😉
0x0000 00 25 b3 bf 91 ee 00 21 29 66 71 95 08 00 45 00
0x0010 00 3c 06 7b 00 00 7f 01 6a eleven c0 a8 00 80 0a 0a
0x0020 00 03 00 00 55 36 00 01 00 25 61 62 63 64 65 66
0x0030 67 68 69 6a 6b 6c 6d 6e 6f seventy 71 72 73 74 75 76
0x0040 77 61 62 63 64 65 66 67 68 69 Conclusion
Hexadecimal may seem like gibberish and very complicated at first, just afterward analyzing a couple of packets with the help of some cheat-sheets, of course, you volition find it very easy and sometimes agreeable! not to mention that this skill is necessary for any cybersecurity annotator or a forensics investigator.
Notation: I've written this story as a cheat-sheet for myself while practicing and idea information technology might help somebody. I'd appreciate your feedback. Thank You!
Source: https://medium.com/@amgedwageh/network-packet-manual-analysis-63e25f32ea54
Post a Comment for "How Do You Know Packet Is Icmp From Hex"